I thought about using some "anonymous browsing" software but then I have to trust that service and I have no idea who they are. This article outlines my solution; which is to run a web proxy on my home system, set up an encrypted SSL tunnel between my laptop and my home system which sends packets to the web proxy, and set the browser on the laptop to use the laptop end of the SSL tunnel as the web proxy (see figure 1). All web traffic - including my E-mail goes through the encrypted tunnel. In addition since the web proxy on my home system is the software actually accessing the web pages - it is doing the DNS queries so my laptop does not leak information like my banking site. Granted I have to trust my home's ISP but I rather trust them then some airport, coffee shop or hotel ISP.
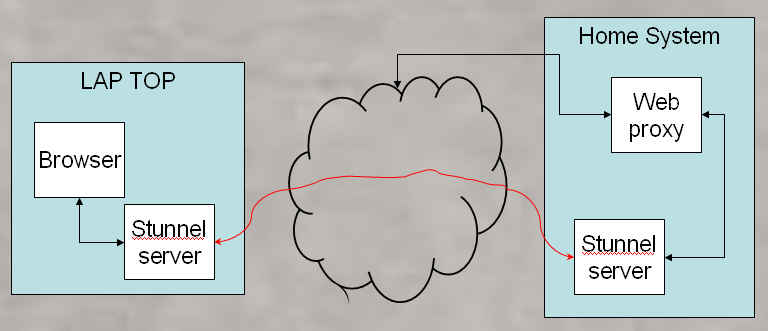
I'll outline the steps needed to set this up and then go into the details. Note that the SSL tunnel and web proxy software all run under MS Windows, although you could do the same thing using some other operating system.
1) down load and install stunnel
Stunnel is the software that sets up the SSL tunnel you can find stunnel at www.stunnel.org. The version I am using is 4.25. Once installed you can set stunnel up to run as a service or just run it manually. I run it manually when I know I will need it.
2) down load and install a web proxy
There are many web proxies out there; I like WebScarab because it keeps a record of all the web pages that I access. It is amazing where some site take you. It also lets you do things like display hidden fields. You can find WebScarab at www.owasp.org/index.php/OWASP_WebScarab_Project.
Unfortunately, the process is not well documented or at least I couldn't find anything that I thought described the process is simple easy to follow steps.
Hence the following. Unfortunately, the steps outlined here require a Linux system. I downloaded the Ubuntu distribution (www.ubuntu.com) and used the live CD aspect so I didn't need to actually install it. I wrote the certificates to a USB flash disk so they would be available when I booted back to Windows.
The following is an annotated log of the steps that I followed from within a terminal (aka Command) window. Underlined characters are characters that I typed. Text with a blue-ish background are my annotations. Note that no special privileges are needed.
On both client and server the first thing I suggest that you do is, with the exception of the NODELAY lines and maybe the debug line, place a comment indication, the semi-colon character, in front of every line that doesn't already have one.
Then on the server configuration file add the following lines immediately before the service level configuration entries. These are labeled with a comment in the file:
And at the end of the server configuration file add the lines
This creates a "stunnel" service that listening on port 119 and sends all traffic that it receives to the localhost at port 8008. This is the port that webscarab listens to by default.
The selection of the accept port may be significant. If your ISP is like mine they frown on people with "home" accounts running servers and certain port numbers, like, 80, 8080 and 8008 are blocked. It may take some experimentation to figure out what ports are allowed. In addition if you are have a firewall between your Internet access modem and your local network you will need to configure it to allow connection requests on that point through.
In the client configuration file remove the semicolon from the beginning of the "client = yes" line. Then add the 3 lines immediately before the service level configuration entries. These are labeled with a comment in the file:
Note that these lines are slightly different from the lines added to the server configuration file. The "cert" line identifies the file containing the key and cert for the current host, i.e. the server has stunnel_server.pem and the client has stunnel_client.pem. The CAfile has the file containing the other host's key and cert as well as the CA's key and cert.
Finally at the end of the client configuration file add the stunnel service lines
This tells stunnel to listen on port 8080 and send all traffic to the stunnel server at 192.168.1.50 listening on port 119. Note that 119 corresponds to the accept port in the stunnel server's configuration file.
This is my server stunnel.conf file
And this is my client stunnel.conf file
Exactly how you do this will depend on your browser
For IE7 select "Internet Options" from the Tools menu then select the Connections tab and click on the "LAN settings" button. Select the "Use a proxy server for your LAN" and fill in the address and port number.
For Firefox 3, select Options from the tools menu then select the Network tab under the Advanced options. For there click on the Settings button and select Manual proxy configuration and fill in the address and port number.
For other browsers you are on your own.
3) create a set of certificates
The certificates are needed so that the client and server can identify each other. This is really the only tricky part. If you want you can use the certificate that stunnel comes with BUT that will mean that anyone who knows what port stunnel is listening on will be able to connect to your tunnel.
Immediately after starting Ubuntu and logging in this is the
contents of your home dir. I'll point out additions as we proceed
ubuntu@ubuntu:~$ ls
Desktop Documents Music Pictures Public Templates Videos
This command will start the process of creating a certificate authority.
This is the authority that generates and signs the other certificates.
Its location is not in $PATH, the list of directories used to locate
commands, so you have to refer to it with an absolute path
ubuntu@ubuntu:~$ /usr/lib/ssl/misc/CA.pl -newca
CA certificate filename (or enter to create) While you cannot see it, I typed "enter" here to create
Making CA certificate ...
Generating a 1024 bit RSA private key
......++++++
........................................................++++++
writing new private key to './demoCA/private/cakey.pem'
Enter PEM pass phrase: You can't see this either but I typed passphrase as my pass phrase
Verifying - Enter PEM pass phrase: Type it again
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:US
State or Province Name (full name) [Some-State]:Arizona
Locality Name (eg, city) []:Phoenix
Organization Name (eg, company) [Internet Widgits Pty Ltd]:FBN
Organizational Unit Name (eg, section) []:CA I give each certificate a unit name that will
make it easy to identify, i.e. CA for certificate
authory and server and client for the server and
client certificates
Common Name (eg, YOUR name) []:Noah Davids
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
Using configuration from /usr/lib/ssl/openssl.cnf
Enter pass phrase for ./demoCA/private/cakey.pem: Type in the pass phrase passphrase again
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number:
f4:22:3f:64:6d:d0:8f:e8
Validity
Not Before: Aug 24 14:05:38 2008 GMT
Not After : Aug 24 14:05:38 2011 GMT
Subject:
countryName = US
stateOrProvinceName = Arizona
organizationName = FBN
organizationalUnitName = CA
commonName = Noah Davids
X509v3 extensions:
X509v3 Subject Key Identifier:
0C:1C:B8:51:B0:D4:5B:EA:E4:B0:02:FE:5D:55:80:D7:17:FE:78:3D
X509v3 Authority Key Identifier:
keyid:0C:1C:B8:51:B0:D4:5B:EA:E4:B0:02:FE:5D:55:80:D7:17:FE:78:3D
DirName:/C=US/ST=Arizona/O=FBN/OU=CA/CN=Noah Davids
serial:F4:22:3F:64:6D:D0:8F:E8
X509v3 Basic Constraints:
CA:TRUE
Certificate is to be certified until Aug 24 14:05:38 2011 GMT (1095 days)
Write out database with 1 new entries
Data Base Updated
We now have a new directory named demoCA
ubuntu@ubuntu:~$ ls
demoCA Desktop Documents Music Pictures Public Templates Videos
This is the contents of that directory.
ubuntu@ubuntu:~$ find demoCA
demoCA
demoCA/index.txt.attr
demoCA/index.txt
demoCA/index.txt.old
demoCA/serial
demoCA/cacert.pem
demoCA/careq.pem
demoCA/crlnumber
demoCA/private
demoCA/private/cakey.pem
demoCA/newcerts
demoCA/newcerts/F4223F646DD08FE8.pem
demoCA/crl
demoCA/certs
Now that the Certificate Authority is created we can create the certificates needed
by the stunnel client and server. First we need to create a certificate request
ubuntu@ubuntu:~$ /usr/lib/ssl/misc/CA.pl -newreq
Generating a 1024 bit RSA private key
.............................................................++++++
....++++++
writing new private key to 'newkey.pem'
Enter PEM pass phrase: Again we need a pass phrase, keep it simple and use passphrase again
Verifying - Enter PEM pass phrase: Type it in again
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:US
State or Province Name (full name) [Some-State]:Arizona
Locality Name (eg, city) []:Phoenix
Organization Name (eg, company) [Internet Widgits Pty Ltd]:FBN
Organizational Unit Name (eg, section) []:Server Since this will be the certificate for the stunnel server
I name the OU server
Common Name (eg, YOUR name) []:Noah Davids
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
Request is in newreq.pem, private key is in newkey.pem
The request has been created note that we now have newkey.pem and newreq.pem files
ubuntu@ubuntu:~$ ls
demoCA Documents newkey.pem Pictures Templates
Desktop Music newreq.pem Public Videos
Now we create the certificate
ubuntu@ubuntu:~$ /usr/lib/ssl/misc/CA.pl -sign
Using configuration from /usr/lib/ssl/openssl.cnf
Enter pass phrase for ./demoCA/private/cakey.pem:Type the pass phrase here
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number:
f4:22:3f:64:6d:d0:8f:e9
Validity
Not Before: Aug 24 14:07:38 2008 GMT
Not After : Aug 24 14:07:38 2009 GMT
Subject:
countryName = US
stateOrProvinceName = Arizona
localityName = Phoenix
organizationName = FBN
organizationalUnitName = Server
commonName = Noah Davids
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
6B:D1:B1:A9:84:D5:90:1C:FD:76:74:E5:3F:A4:E7:7E:AC:1D:58:5F
X509v3 Authority Key Identifier:
keyid:0C:1C:B8:51:B0:D4:5B:EA:E4:B0:02:FE:5D:55:80:D7:17:FE:78:3D
Certificate is to be certified until Aug 24 14:07:38 2009 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
Signed certificate is in newcert.pem
And we now have a newcert.pem
ubuntu@ubuntu:~$ ls
demoCA Documents newcert.pem newreq.pem Public Videos
Desktop Music newkey.pem Pictures Templates
If you display the newkey.pem you will see that it is an RSA PRIVATE KEY
and that it is ENCRYPTED. The pass phrase is what is used to decrypt the key.
ubuntu@ubuntu:~$ cat newkey.pem
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: DES-EDE3-CBC,7DA5FEC84D422C6D
i0HGExUNcNg0Qg4L03gT1Sad9DkDCtWlmu3CWkOV5VPb3lQex0MgAIWLERXOb/06
jSVLaCSBA3oDFMnJUqxr8M1oYZKnh22grx+a+cfSvOp12DXrt2pVsiy1UimlyR8P
A8LkaC21MKe+or4hp867y74hme2zx+Os9zG0H36jRuszHn/KHVbcLI0s420OXHAZ
UGAeECgXNKc6mGOg+/NTfztEI0pBv8o1zpjUWwv+cFdx+vuS2sgR7i68rCdMwkgj
4lZItWOIlK4H0yxCm0aOlzJaizi//yWLtg+L/qdPuYuWSo3CKBNutBs7ovqfx+9V
KifwLoglcDRQueW6ix78z0WJ7Fl6vNWd26errkqMe/luH3tgJAePAI6uyFaEx5Yt
Tn+ZXb5ht58ouVm1hsjQ5/mTWsNVOvIx4Hbpo/ydCbN3B5N+n2AWV0Z82ObjaUpc
yLEFMuhAhgfgS4lUqGkNPe32xvyIHqLGMQcG9qLgkI7MpDd/LvVIi83vdeBuNP/E
wu9JW3cmTAPiltUCBeXMPDKXui43AEJ5rRAv3fy2SPx3WxalaYMO4mH4yR3iCeU/
R0nW/EKEt85G25X48SHs3QjPKQWRr+0kQ61iHf6w1kbmkMgsT8Z4zb7nlAVib1jq
VEpk4NCDTAfeqPt2Uy1PzgyCm7oGs/1Q+o5gC7nPbwKm6EYTTzgRVuYn4i4L/BIY
Fe797OByz4CTd5IT1yXMeBGG1H5zX3W3lM6XcPklPZQBQHPsMpHqXe1CxPGBmBbM
6+HtGvW8iMXw+OSwnjt11ySqE2pAFwB3Xaw9+Xn/zGDNNhh62C6aXg==
-----END RSA PRIVATE KEY-----
Stunnel cannot use the encrypted key so we have to remove the pass phrase.
Unlike the CA.pl macro the openssl command is in the $PATH so we do not
need to provide an absolute path. Since this is the key for the server
we will call it server_key.pem
ubuntu@ubuntu:~$ openssl rsa -in newkey.pem -out server_key.pem
Enter pass phrase for newkey.pem:Type the pass phrase here
writing RSA key
Note that this server_key.pem does not have the ENCRYPTED lines
ubuntu@ubuntu:~$ cat server_key.pem
-----BEGIN RSA PRIVATE KEY-----
MIICXAIBAAKBgQDWRm2rMZmTQBvP9ocAWg3O9oFh/UktcabmNxrwS+/xeE5SSQ+A
gMrN1qwVxcqu7PA4htPzjD0/9qZEKXMIsQ0OyyzzgnKs/czh0VZ2irf+g8q/pmRu
/JD1SDsTz2S3AUzcgy0pY1cKGF90i0sDii7ORW4q/Fmzhn+bWp0UCL+tvQIDAQAB
AoGAJCu5YZe62/+LclykR2vsPs6f4qG2E6TGzr/onT3EYFe1qPBKXJ/hHEQrwnUk
FMlMd85Swx8eS8jgIkt47rOsh06tqrpQ26RiWfGYur1uKFuyt9l3qinGWQbkrxLq
f9WdKZGVcm1AEocaeBjkmkCzt9KqNiSH+64kGHkVV2R1TKUCQQDwOezR+2yLU6NS
ExwK4PweIGuJhOzRpeuBRuz1r0MTATvrWkqVOKXDuxiMA5CPCkutuIjRH9Z+SOLt
eExOA3kDAkEA5FhHOkxlpqen4Pf0eHXlFPNYqseuv6bHeZRgD++n/mDABfh+/RTu
xjzBjRbUBiKH88iW+ZZffl9u1hyloBuiPwJAcZJxLDU59ATuyfbO4zXK/FNHhBSc
AeH3nX7yuJTLmUiUE4j0iefmNstVp5xn07iCXvdHd9cdiUbcQnkFWjy6EQJBAM+z
bLaenyfEAHQlln2r3z/7SX+uOkmhjngMeoSEXa6ImqHTss7Jp5cx1Gxdg2ZBKqCY
qJtGKH5umAax8AV+nUkCQGux+PFHy+P7v1KcShKvsDUCo81wh839inVA1HqoXF+y
rwdaxsqI8QH7pPgBHN3PpwIwHbrG0vrivRn2xGASaFA=
-----END RSA PRIVATE KEY-----
Rename the server certificate from newcert.pem to server_cert.pem. We are
going to need the text of the encrypted certificate later so I display it here
ubuntu@ubuntu:~$ cp newcert.pem server_cert.pem
ubuntu@ubuntu:~$ cat server_cert.pem
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
f4:22:3f:64:6d:d0:8f:e9
Signature Algorithm: sha1WithRSAEncryption
Issuer: C=US, ST=Arizona, O=FBN, OU=CA, CN=Noah Davids
Validity
Not Before: Aug 24 14:07:38 2008 GMT
Not After : Aug 24 14:07:38 2009 GMT
Subject: C=US, ST=Arizona, L=Phoenix, O=FBN, OU=Server, CN=Noah Davids
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (1024 bit)
Modulus (1024 bit):
00:d6:46:6d:ab:31:99:93:40:1b:cf:f6:87:00:5a:
0d:ce:f6:81:61:fd:49:2d:71:a6:e6:37:1a:f0:4b:
ef:f1:78:4e:52:49:0f:80:80:ca:cd:d6:ac:15:c5:
ca:ae:ec:f0:38:86:d3:f3:8c:3d:3f:f6:a6:44:29:
73:08:b1:0d:0e:cb:2c:f3:82:72:ac:fd:cc:e1:d1:
56:76:8a:b7:fe:83:ca:bf:a6:64:6e:fc:90:f5:48:
3b:13:cf:64:b7:01:4c:dc:83:2d:29:63:57:0a:18:
5f:74:8b:4b:03:8a:2e:ce:45:6e:2a:fc:59:b3:86:
7f:9b:5a:9d:14:08:bf:ad:bd
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
6B:D1:B1:A9:84:D5:90:1C:FD:76:74:E5:3F:A4:E7:7E:AC:1D:58:5F
X509v3 Authority Key Identifier:
keyid:0C:1C:B8:51:B0:D4:5B:EA:E4:B0:02:FE:5D:55:80:D7:17:FE:78:3D
Signature Algorithm: sha1WithRSAEncryption
70:39:d7:2d:9a:48:44:44:b4:cc:25:6f:06:be:20:b4:33:00:
6d:f1:fa:13:11:4f:d9:ea:07:a2:c5:e2:09:10:cf:e2:cb:2d:
5b:e0:44:f6:4b:dc:6b:df:38:6e:67:c9:82:23:b6:5e:32:d5:
56:7f:84:74:ae:83:f5:da:40:d8:b6:f4:53:b5:58:a8:09:78:
0d:c7:1b:14:32:0f:a0:0b:13:4c:98:9d:a3:18:71:70:69:a1:
ae:c7:51:0e:3e:ab:67:e9:15:1a:2f:f5:f2:6f:fb:6d:1c:98:
f6:87:d0:53:29:e1:b7:8d:6f:ab:25:9e:a2:aa:be:fd:54:2d:
99:82
-----BEGIN CERTIFICATE-----
MIICrzCCAhigAwIBAgIJAPQiP2Rt0I/pMA0GCSqGSIb3DQEBBQUAMFAxCzAJBgNV
BAYTAlVTMRAwDgYDVQQIEwdBcml6b25hMQwwCgYDVQQKEwNGQk4xCzAJBgNVBAsT
AkNBMRQwEgYDVQQDEwtOb2FoIERhdmlkczAeFw0wODA4MjQxNDA3MzhaFw0wOTA4
MjQxNDA3MzhaMGYxCzAJBgNVBAYTAlVTMRAwDgYDVQQIEwdBcml6b25hMRAwDgYD
VQQHEwdQaG9lbml4MQwwCgYDVQQKEwNGQk4xDzANBgNVBAsTBlNlcnZlcjEUMBIG
A1UEAxMLTm9haCBEYXZpZHMwgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBANZG
basxmZNAG8/2hwBaDc72gWH9SS1xpuY3GvBL7/F4TlJJD4CAys3WrBXFyq7s8DiG
0/OMPT/2pkQpcwixDQ7LLPOCcqz9zOHRVnaKt/6Dyr+mZG78kPVIOxPPZLcBTNyD
LSljVwoYX3SLSwOKLs5Fbir8WbOGf5tanRQIv629AgMBAAGjezB5MAkGA1UdEwQC
MAAwLAYJYIZIAYb4QgENBB8WHU9wZW5TU0wgR2VuZXJhdGVkIENlcnRpZmljYXRl
MB0GA1UdDgQWBBRr0bGphNWQHP12dOU/pOd+rB1YXzAfBgNVHSMEGDAWgBQMHLhR
sNRb6uSwAv5dVYDXF/54PTANBgkqhkiG9w0BAQUFAAOBgQBwOdctmkhERLTMJW8G
viC0MwBt8foTEU/Z6geixeIJEM/iyy1b4ET2S9xr3zhuZ8mCI7ZeMtVWf4R0roP1
2kDYtvRTtVioCXgNxxsUMg+gCxNMmJ2jGHFwaaGux1EOPqtn6RUaL/Xyb/ttHJj2
h9BTKeG3jW+rJZ6iqr79VC2Zgg==
-----END CERTIFICATE-----
We have a server_cert.pem and a server_key.pem but the new*pem
files are still hanging around.
ubuntu@ubuntu:~$ ls
demoCA Music newreq.pem server_cert.pem Videos
Desktop newcert.pem Pictures server_key.pem
Documents newkey.pem Public Templates
I delete the new*pem files just to make sure that client certificate creation
process doesn't get confused. I know its not necessary but I can't help myself
ubuntu@ubuntu:~$ rm new*
Yes, the files are really gone
ubuntu@ubuntu:~$ ls
demoCA Documents Pictures server_cert.pem Templates
Desktop Music Public server_key.pem Videos
Create the client certificate request. This is exactly the same process
as the server certificate reques, except the OU is client instead of server
ubuntu@ubuntu:~$ /usr/lib/ssl/misc/CA.pl -newreq
Generating a 1024 bit RSA private key
...++++++
.....................++++++
writing new private key to 'newkey.pem'
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:US
State or Province Name (full name) [Some-State]:Arizona
Locality Name (eg, city) []:Phoenix
Organization Name (eg, company) [Internet Widgits Pty Ltd]:FBN
Organizational Unit Name (eg, section) []:Client
Common Name (eg, YOUR name) []:Noah Davids
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
Request is in newreq.pem, private key is in newkey.pem
Now we create the certificate
ubuntu@ubuntu:~$ /usr/lib/ssl/misc/CA.pl -sign
Using configuration from /usr/lib/ssl/openssl.cnf
Enter pass phrase for ./demoCA/private/cakey.pem:Type the pass phrase here
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number:
f4:22:3f:64:6d:d0:8f:ea
Validity
Not Before: Aug 24 14:13:29 2008 GMT
Not After : Aug 24 14:13:29 2009 GMT
Subject:
countryName = US
stateOrProvinceName = Arizona
localityName = Phoenix
organizationName = FBN
organizationalUnitName = Client
commonName = Noah Davids
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
FF:F1:15:E1:04:53:E5:26:71:10:90:B6:A6:3F:8C:89:B8:BC:BE:FF
X509v3 Authority Key Identifier:
keyid:0C:1C:B8:51:B0:D4:5B:EA:E4:B0:02:FE:5D:55:80:D7:17:FE:78:3D
Certificate is to be certified until Aug 24 14:13:29 2009 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
Signed certificate is in newcert.pem
Remove the pass phrase encryption from the client key and rename it client_key.pem
ubuntu@ubuntu:~$ openssl rsa -in newkey.pem -out client_key.pem
Enter pass phrase for newkey.pem:Type the pass phrase
writing RSA key
Copy the certificate to client_cert.pem
ubuntu@ubuntu:~$ cp newcert.pem client_cert.pem
Display the client_key.pem
ubuntu@ubuntu:~$ cat client_key.pem
-----BEGIN RSA PRIVATE KEY-----
MIICXQIBAAKBgQDhZk9oF8B5t9fiwsTBMdeC9RqkTDoVmAFqOqtbOPoLkFHhe6B6
uSc9LTW5qvm2CNjfH2Whtf7kvYj6ROPtP2z2yBt0gHy68/RU4xI0jnPkvYDVye4r
BhYBBCdRN1oSIfgX+KrjsPttOPvQVh4NnCZ2QVqelryIy2XrxR2qldaeOwIDAQAB
AoGAZd4qVx4c9CW9YROrfrD6+Imzz7tPqQC46vy3AxReFanVB7Yq0iwp6sEq/c2i
671V3ok/EnXBTDnI1WsbI9c9c/WeQxRdvdABJhx0vPdiZ/x08WeQQeh9XjnimlAV
UnJB9FMD/WMP4JHw8TnJGsnUNjkP9dInVqRm52Ak1XqQB3ECQQD773UvuIoG9xDA
mUpYgW9lHo8u4q8HwWxczfBiIkVKG8PO/oImS1PNhT2R6UGE4uXJ1m+BReKqRJMu
CrJR1MlpAkEA5QlBMkigt8G9eEyzp4gRN1MbvXknD1ZuyT1+cC7rS+ZDZ3FhNn4/
wxvCQQS18G4zRkrUTes4X3fdi+n/APvyAwJBALncneqXzRR4Xx6HuGZ1DxZdpipj
x9cD5orMz4PGXrHeq+Vgs+nGdsvPeW3U1KZRsk7maRrI0QDmWGKGN6nRPskCQCPk
JWFZ3EWviJ93dZfFTN1cmrZAbAyNQOMsTcoKsDi+psVpERDXC+rpSLGjqVc6DbLw
OwDS4YykXgV0788ZrD0CQQCbe+VkCVX1Nyrqgylpnza+W75p+A5YUC7kZgvls2kG
sr5+BAyyOPpTiUao+l3ib15udCxJmw+qEYSq8TQEaLpG
-----END RSA PRIVATE KEY-----
Now display the client_cert.pem
ubuntu@ubuntu:~$ cat client_cert.pem
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
f4:22:3f:64:6d:d0:8f:ea
Signature Algorithm: sha1WithRSAEncryption
Issuer: C=US, ST=Arizona, O=FBN, OU=CA, CN=Noah Davids
Validity
Not Before: Aug 24 14:13:29 2008 GMT
Not After : Aug 24 14:13:29 2009 GMT
Subject: C=US, ST=Arizona, L=Phoenix, O=FBN, OU=Client, CN=Noah Davids
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (1024 bit)
Modulus (1024 bit):
00:e1:66:4f:68:17:c0:79:b7:d7:e2:c2:c4:c1:31:
d7:82:f5:1a:a4:4c:3a:15:98:01:6a:3a:ab:5b:38:
fa:0b:90:51:e1:7b:a0:7a:b9:27:3d:2d:35:b9:aa:
f9:b6:08:d8:df:1f:65:a1:b5:fe:e4:bd:88:fa:44:
e3:ed:3f:6c:f6:c8:1b:74:80:7c:ba:f3:f4:54:e3:
12:34:8e:73:e4:bd:80:d5:c9:ee:2b:06:16:01:04:
27:51:37:5a:12:21:f8:17:f8:aa:e3:b0:fb:6d:38:
fb:d0:56:1e:0d:9c:26:76:41:5a:9e:96:bc:88:cb:
65:eb:c5:1d:aa:95:d6:9e:3b
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
FF:F1:15:E1:04:53:E5:26:71:10:90:B6:A6:3F:8C:89:B8:BC:BE:FF
X509v3 Authority Key Identifier:
keyid:0C:1C:B8:51:B0:D4:5B:EA:E4:B0:02:FE:5D:55:80:D7:17:FE:78:3D
Signature Algorithm: sha1WithRSAEncryption
49:bf:39:fd:0f:17:94:e7:a4:8a:5d:a5:5a:b3:55:f2:08:9d:
2d:cb:e7:03:74:7f:db:96:0e:3b:e2:ec:c9:af:6e:47:73:76:
6a:59:fe:0a:04:cb:a8:86:aa:c7:90:03:b8:6f:57:f5:27:03:
4c:8f:50:1e:b5:5c:72:b2:4d:11:6a:1c:75:b8:21:e3:cc:22:
87:8e:da:6e:8f:59:1c:ff:e7:e3:1f:6a:04:23:55:18:64:a8:
52:8b:57:46:d9:fd:ef:f4:1b:98:5a:35:42:a6:05:44:64:ba:
73:2d:e2:ca:97:f6:e2:6c:07:00:6c:77:b7:73:d8:3b:dd:75:
a9:f9
-----BEGIN CERTIFICATE-----
MIICrzCCAhigAwIBAgIJAPQiP2Rt0I/qMA0GCSqGSIb3DQEBBQUAMFAxCzAJBgNV
BAYTAlVTMRAwDgYDVQQIEwdBcml6b25hMQwwCgYDVQQKEwNGQk4xCzAJBgNVBAsT
AkNBMRQwEgYDVQQDEwtOb2FoIERhdmlkczAeFw0wODA4MjQxNDEzMjlaFw0wOTA4
MjQxNDEzMjlaMGYxCzAJBgNVBAYTAlVTMRAwDgYDVQQIEwdBcml6b25hMRAwDgYD
VQQHEwdQaG9lbml4MQwwCgYDVQQKEwNGQk4xDzANBgNVBAsTBkNsaWVudDEUMBIG
A1UEAxMLTm9haCBEYXZpZHMwgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBAOFm
T2gXwHm31+LCxMEx14L1GqRMOhWYAWo6q1s4+guQUeF7oHq5Jz0tNbmq+bYI2N8f
ZaG1/uS9iPpE4+0/bPbIG3SAfLrz9FTjEjSOc+S9gNXJ7isGFgEEJ1E3WhIh+Bf4
quOw+204+9BWHg2cJnZBWp6WvIjLZevFHaqV1p47AgMBAAGjezB5MAkGA1UdEwQC
MAAwLAYJYIZIAYb4QgENBB8WHU9wZW5TU0wgR2VuZXJhdGVkIENlcnRpZmljYXRl
MB0GA1UdDgQWBBT/8RXhBFPlJnEQkLamP4yJuLy+/zAfBgNVHSMEGDAWgBQMHLhR
sNRb6uSwAv5dVYDXF/54PTANBgkqhkiG9w0BAQUFAAOBgQBJvzn9DxeU56SKXaVa
s1XyCJ0ty+cDdH/blg474uzJr25Hc3ZqWf4KBMuohqrHkAO4b1f1JwNMj1AetVxy
sk0Rahx1uCHjzCKHjtpuj1kc/+fjH2oEI1UYZKhSi1dG2f3v9BuYWjVCpgVEZLpz
LeLKl/bibAcAbHe3c9g73XWp+Q==
-----END CERTIFICATE-----
Will will also need an unencrypted copy of the Certificate Authorities key
ubuntu@ubuntu:~$ openssl rsa -in ./demoCA/private/cakey.pem -out ca_key.pem
Enter pass phrase for ./demoCA/private/cakey.pem:Type the pass phrase here
writing RSA key
Copy the Certificate Authority's (CA's) certificate as well.
Not strictly needed since we could just display in where it
is but this way everything we need is in 1 place.
ubuntu@ubuntu:~$ cp ./demoCA/cacert.pem ca_cert.pem
Display the CA's unencrypted key
ubuntu@ubuntu:~$ cat ca_key.pem
-----BEGIN RSA PRIVATE KEY-----
MIICXQIBAAKBgQCjFUVhee/3RvapaM+JyGETO1mZsBcQ/+k0W8IC/OClKc8hH1ML
YWCt7WuRTZ7tL6YGn/rfx0xlMiN65ebyrioV8W0t4g17CL3f5+e0UqiCUF1sUfW2
zVP0s+2UDyKFCX2lScY+4MHr6aE5fyKFkOSmQwjFYa+/MB5VICln4CYBGwIDAQAB
AoGAGAh4cwb/QBerHggeHZX0CFuEtstmetDb0yV6j+ooSO7CYYU2PcUZ9Ee6xG0F
8LpG408ML5I1Rex/ogrjX/weo2T5tsf7C0TxoJRUu4F6yQ8VUBbZ1z+2HZzw29Fi
y4pax8xUBYlU/aqBd0rqEZyNW40tDRjmrIfOH7t/wIng5ZECQQDMpP007DemQdN+
IQS+e/+q3TXkTjuGSXNoShqwCkJ0zUOBE4sWsCSCwWp2ZF44a7dx/of+050FAcH6
3DrDYdadAkEAzAI+8eR6JcLH0L7lsxKgLaDj/RwAZ7bDKaULXOes8pEMFePLxLN+
yY32QPQbZrUMAzo1mDJ0KrkiczD454DNFwJAf9nUF2w8mDIn33ThceAmKqlpMelu
ZsccwtsJMVI3kqFquwlqrBH/vXD5Al5SPw2M3jsW2615O9eNSRyt2cMWQQJBAIdB
+e+wlteQU6Bv4KUgdTirUl1PAmnA/5YNygHXzI+qYUPmGwSYKTiCucEI1136LTO6
lSwKT4C/7DpJPs1mVRMCQQCD8fqwCs0RWo9chugoHh3nrI9VXzDvglz2O5DGgdiS
RAwwWU5P0+G1m71jjeB447/bCHm+DzP2xHlIlh0Gf7Pr
-----END RSA PRIVATE KEY-----
And display the CA's certificate
ubuntu@ubuntu:~$ cat ca_cert.pem
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
f4:22:3f:64:6d:d0:8f:e8
Signature Algorithm: sha1WithRSAEncryption
Issuer: C=US, ST=Arizona, O=FBN, OU=CA, CN=Noah Davids
Validity
Not Before: Aug 24 14:05:38 2008 GMT
Not After : Aug 24 14:05:38 2011 GMT
Subject: C=US, ST=Arizona, O=FBN, OU=CA, CN=Noah Davids
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (1024 bit)
Modulus (1024 bit):
00:a3:15:45:61:79:ef:f7:46:f6:a9:68:cf:89:c8:
61:13:3b:59:99:b0:17:10:ff:e9:34:5b:c2:02:fc:
e0:a5:29:cf:21:1f:53:0b:61:60:ad:ed:6b:91:4d:
9e:ed:2f:a6:06:9f:fa:df:c7:4c:65:32:23:7a:e5:
e6:f2:ae:2a:15:f1:6d:2d:e2:0d:7b:08:bd:df:e7:
e7:b4:52:a8:82:50:5d:6c:51:f5:b6:cd:53:f4:b3:
ed:94:0f:22:85:09:7d:a5:49:c6:3e:e0:c1:eb:e9:
a1:39:7f:22:85:90:e4:a6:43:08:c5:61:af:bf:30:
1e:55:20:29:67:e0:26:01:1b
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
0C:1C:B8:51:B0:D4:5B:EA:E4:B0:02:FE:5D:55:80:D7:17:FE:78:3D
X509v3 Authority Key Identifier:
keyid:0C:1C:B8:51:B0:D4:5B:EA:E4:B0:02:FE:5D:55:80:D7:17:FE:78:3D
DirName:/C=US/ST=Arizona/O=FBN/OU=CA/CN=Noah Davids
serial:F4:22:3F:64:6D:D0:8F:E8
X509v3 Basic Constraints:
CA:TRUE
Signature Algorithm: sha1WithRSAEncryption
96:43:e8:de:7d:e6:f7:0b:5e:70:7d:12:12:86:58:20:c2:b9:
3b:e4:b8:b7:1a:13:71:61:75:c7:9c:1b:eb:70:62:14:c2:9c:
6c:1e:cd:59:3e:36:06:aa:93:13:36:8d:1e:ee:9c:7b:f7:df:
2c:db:cc:07:88:36:2b:0e:29:7f:e2:3a:45:66:71:f7:f2:2d:
9f:72:d9:ac:3a:dd:1d:ac:b7:b9:21:da:5b:f9:27:2a:ed:7c:
39:30:72:f2:39:6b:ce:4b:43:57:ec:42:9e:9c:45:e7:f2:3f:
fc:1b:14:3f:6d:0a:df:65:61:7d:56:e6:9d:6a:56:e1:0d:16:
c6:f7
-----BEGIN CERTIFICATE-----
MIIC0jCCAjugAwIBAgIJAPQiP2Rt0I/oMA0GCSqGSIb3DQEBBQUAMFAxCzAJBgNV
BAYTAlVTMRAwDgYDVQQIEwdBcml6b25hMQwwCgYDVQQKEwNGQk4xCzAJBgNVBAsT
AkNBMRQwEgYDVQQDEwtOb2FoIERhdmlkczAeFw0wODA4MjQxNDA1MzhaFw0xMTA4
MjQxNDA1MzhaMFAxCzAJBgNVBAYTAlVTMRAwDgYDVQQIEwdBcml6b25hMQwwCgYD
VQQKEwNGQk4xCzAJBgNVBAsTAkNBMRQwEgYDVQQDEwtOb2FoIERhdmlkczCBnzAN
BgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEAoxVFYXnv90b2qWjPichhEztZmbAXEP/p
NFvCAvzgpSnPIR9TC2Fgre1rkU2e7S+mBp/638dMZTIjeuXm8q4qFfFtLeINewi9
3+fntFKoglBdbFH1ts1T9LPtlA8ihQl9pUnGPuDB6+mhOX8ihZDkpkMIxWGvvzAe
VSApZ+AmARsCAwEAAaOBszCBsDAdBgNVHQ4EFgQUDBy4UbDUW+rksAL+XVWA1xf+
eD0wgYAGA1UdIwR5MHeAFAwcuFGw1Fvq5LAC/l1VgNcX/ng9oVSkUjBQMQswCQYD
VQQGEwJVUzEQMA4GA1UECBMHQXJpem9uYTEMMAoGA1UEChMDRkJOMQswCQYDVQQL
EwJDQTEUMBIGA1UEAxMLTm9haCBEYXZpZHOCCQD0Ij9kbdCP6DAMBgNVHRMEBTAD
AQH/MA0GCSqGSIb3DQEBBQUAA4GBAJZD6N595vcLXnB9EhKGWCDCuTvkuLcaE3Fh
dcecG+twYhTCnGwezVk+NgaqkxM2jR7unHv33yzbzAeINisOKX/iOkVmcffyLZ9y
2aw63R2st7kh2lv5JyrtfDkwcvI5a85LQ1fsQp6cRefyP/wbFD9tCt9lYX1W5p1q
VuENFsb3
-----END CERTIFICATE-----
Once you have the certificates and keys you will need to build four files,
1) stunnel_client.pem - containing the client's private key and certificate
2) stunnel_server.pem - containing the server's private key and certificate
3) stunnel_client_ca.pem - containing the client's key and certificate and the
CA's key and certificate
4) stunnel_server_ca.pem - containing the server's key and certificate and the
CA's key and certificate
The reason you need to include the CA's key and certificate is that stunnel needs to be
able to verify the client and server's certificate with the CA and since the CA was a
temporary system stunnel cannot do this unless it has the CA's key and certificate.
The four files look like:
stunnel_client.pem
-----BEGIN RSA PRIVATE KEY-----
MIICXQIBAAKBgQDhZk9oF8B5t9fiwsTBMdeC9RqkTDoVmAFqOqtbOPoLkFHhe6B6
uSc9LTW5qvm2CNjfH2Whtf7kvYj6ROPtP2z2yBt0gHy68/RU4xI0jnPkvYDVye4r
BhYBBCdRN1oSIfgX+KrjsPttOPvQVh4NnCZ2QVqelryIy2XrxR2qldaeOwIDAQAB
AoGAZd4qVx4c9CW9YROrfrD6+Imzz7tPqQC46vy3AxReFanVB7Yq0iwp6sEq/c2i
671V3ok/EnXBTDnI1WsbI9c9c/WeQxRdvdABJhx0vPdiZ/x08WeQQeh9XjnimlAV
UnJB9FMD/WMP4JHw8TnJGsnUNjkP9dInVqRm52Ak1XqQB3ECQQD773UvuIoG9xDA
mUpYgW9lHo8u4q8HwWxczfBiIkVKG8PO/oImS1PNhT2R6UGE4uXJ1m+BReKqRJMu
CrJR1MlpAkEA5QlBMkigt8G9eEyzp4gRN1MbvXknD1ZuyT1+cC7rS+ZDZ3FhNn4/
wxvCQQS18G4zRkrUTes4X3fdi+n/APvyAwJBALncneqXzRR4Xx6HuGZ1DxZdpipj
x9cD5orMz4PGXrHeq+Vgs+nGdsvPeW3U1KZRsk7maRrI0QDmWGKGN6nRPskCQCPk
JWFZ3EWviJ93dZfFTN1cmrZAbAyNQOMsTcoKsDi+psVpERDXC+rpSLGjqVc6DbLw
OwDS4YykXgV0788ZrD0CQQCbe+VkCVX1Nyrqgylpnza+W75p+A5YUC7kZgvls2kG
sr5+BAyyOPpTiUao+l3ib15udCxJmw+qEYSq8TQEaLpG
-----END RSA PRIVATE KEY-----
-----BEGIN CERTIFICATE-----
MIICrzCCAhigAwIBAgIJAPQiP2Rt0I/qMA0GCSqGSIb3DQEBBQUAMFAxCzAJBgNV
BAYTAlVTMRAwDgYDVQQIEwdBcml6b25hMQwwCgYDVQQKEwNGQk4xCzAJBgNVBAsT
AkNBMRQwEgYDVQQDEwtOb2FoIERhdmlkczAeFw0wODA4MjQxNDEzMjlaFw0wOTA4
MjQxNDEzMjlaMGYxCzAJBgNVBAYTAlVTMRAwDgYDVQQIEwdBcml6b25hMRAwDgYD
VQQHEwdQaG9lbml4MQwwCgYDVQQKEwNGQk4xDzANBgNVBAsTBkNsaWVudDEUMBIG
A1UEAxMLTm9haCBEYXZpZHMwgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBAOFm
T2gXwHm31+LCxMEx14L1GqRMOhWYAWo6q1s4+guQUeF7oHq5Jz0tNbmq+bYI2N8f
ZaG1/uS9iPpE4+0/bPbIG3SAfLrz9FTjEjSOc+S9gNXJ7isGFgEEJ1E3WhIh+Bf4
quOw+204+9BWHg2cJnZBWp6WvIjLZevFHaqV1p47AgMBAAGjezB5MAkGA1UdEwQC
MAAwLAYJYIZIAYb4QgENBB8WHU9wZW5TU0wgR2VuZXJhdGVkIENlcnRpZmljYXRl
MB0GA1UdDgQWBBT/8RXhBFPlJnEQkLamP4yJuLy+/zAfBgNVHSMEGDAWgBQMHLhR
sNRb6uSwAv5dVYDXF/54PTANBgkqhkiG9w0BAQUFAAOBgQBJvzn9DxeU56SKXaVa
s1XyCJ0ty+cDdH/blg474uzJr25Hc3ZqWf4KBMuohqrHkAO4b1f1JwNMj1AetVxy
sk0Rahx1uCHjzCKHjtpuj1kc/+fjH2oEI1UYZKhSi1dG2f3v9BuYWjVCpgVEZLpz
LeLKl/bibAcAbHe3c9g73XWp+Q==
-----END CERTIFICATE-----
stunnel_server.pem
-----BEGIN RSA PRIVATE KEY-----
MIICXAIBAAKBgQDWRm2rMZmTQBvP9ocAWg3O9oFh/UktcabmNxrwS+/xeE5SSQ+A
gMrN1qwVxcqu7PA4htPzjD0/9qZEKXMIsQ0OyyzzgnKs/czh0VZ2irf+g8q/pmRu
/JD1SDsTz2S3AUzcgy0pY1cKGF90i0sDii7ORW4q/Fmzhn+bWp0UCL+tvQIDAQAB
AoGAJCu5YZe62/+LclykR2vsPs6f4qG2E6TGzr/onT3EYFe1qPBKXJ/hHEQrwnUk
FMlMd85Swx8eS8jgIkt47rOsh06tqrpQ26RiWfGYur1uKFuyt9l3qinGWQbkrxLq
f9WdKZGVcm1AEocaeBjkmkCzt9KqNiSH+64kGHkVV2R1TKUCQQDwOezR+2yLU6NS
ExwK4PweIGuJhOzRpeuBRuz1r0MTATvrWkqVOKXDuxiMA5CPCkutuIjRH9Z+SOLt
eExOA3kDAkEA5FhHOkxlpqen4Pf0eHXlFPNYqseuv6bHeZRgD++n/mDABfh+/RTu
xjzBjRbUBiKH88iW+ZZffl9u1hyloBuiPwJAcZJxLDU59ATuyfbO4zXK/FNHhBSc
AeH3nX7yuJTLmUiUE4j0iefmNstVp5xn07iCXvdHd9cdiUbcQnkFWjy6EQJBAM+z
bLaenyfEAHQlln2r3z/7SX+uOkmhjngMeoSEXa6ImqHTss7Jp5cx1Gxdg2ZBKqCY
qJtGKH5umAax8AV+nUkCQGux+PFHy+P7v1KcShKvsDUCo81wh839inVA1HqoXF+y
rwdaxsqI8QH7pPgBHN3PpwIwHbrG0vrivRn2xGASaFA=
-----END RSA PRIVATE KEY-----
-----BEGIN CERTIFICATE-----
MIICrzCCAhigAwIBAgIJAPQiP2Rt0I/pMA0GCSqGSIb3DQEBBQUAMFAxCzAJBgNV
BAYTAlVTMRAwDgYDVQQIEwdBcml6b25hMQwwCgYDVQQKEwNGQk4xCzAJBgNVBAsT
AkNBMRQwEgYDVQQDEwtOb2FoIERhdmlkczAeFw0wODA4MjQxNDA3MzhaFw0wOTA4
MjQxNDA3MzhaMGYxCzAJBgNVBAYTAlVTMRAwDgYDVQQIEwdBcml6b25hMRAwDgYD
VQQHEwdQaG9lbml4MQwwCgYDVQQKEwNGQk4xDzANBgNVBAsTBlNlcnZlcjEUMBIG
A1UEAxMLTm9haCBEYXZpZHMwgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBANZG
basxmZNAG8/2hwBaDc72gWH9SS1xpuY3GvBL7/F4TlJJD4CAys3WrBXFyq7s8DiG
0/OMPT/2pkQpcwixDQ7LLPOCcqz9zOHRVnaKt/6Dyr+mZG78kPVIOxPPZLcBTNyD
LSljVwoYX3SLSwOKLs5Fbir8WbOGf5tanRQIv629AgMBAAGjezB5MAkGA1UdEwQC
MAAwLAYJYIZIAYb4QgENBB8WHU9wZW5TU0wgR2VuZXJhdGVkIENlcnRpZmljYXRl
MB0GA1UdDgQWBBRr0bGphNWQHP12dOU/pOd+rB1YXzAfBgNVHSMEGDAWgBQMHLhR
sNRb6uSwAv5dVYDXF/54PTANBgkqhkiG9w0BAQUFAAOBgQBwOdctmkhERLTMJW8G
viC0MwBt8foTEU/Z6geixeIJEM/iyy1b4ET2S9xr3zhuZ8mCI7ZeMtVWf4R0roP1
2kDYtvRTtVioCXgNxxsUMg+gCxNMmJ2jGHFwaaGux1EOPqtn6RUaL/Xyb/ttHJj2
h9BTKeG3jW+rJZ6iqr79VC2Zgg==
-----END CERTIFICATE-----
stunnel_client_ca.pem
-----BEGIN RSA PRIVATE KEY-----
MIICXQIBAAKBgQDhZk9oF8B5t9fiwsTBMdeC9RqkTDoVmAFqOqtbOPoLkFHhe6B6
uSc9LTW5qvm2CNjfH2Whtf7kvYj6ROPtP2z2yBt0gHy68/RU4xI0jnPkvYDVye4r
BhYBBCdRN1oSIfgX+KrjsPttOPvQVh4NnCZ2QVqelryIy2XrxR2qldaeOwIDAQAB
AoGAZd4qVx4c9CW9YROrfrD6+Imzz7tPqQC46vy3AxReFanVB7Yq0iwp6sEq/c2i
671V3ok/EnXBTDnI1WsbI9c9c/WeQxRdvdABJhx0vPdiZ/x08WeQQeh9XjnimlAV
UnJB9FMD/WMP4JHw8TnJGsnUNjkP9dInVqRm52Ak1XqQB3ECQQD773UvuIoG9xDA
mUpYgW9lHo8u4q8HwWxczfBiIkVKG8PO/oImS1PNhT2R6UGE4uXJ1m+BReKqRJMu
CrJR1MlpAkEA5QlBMkigt8G9eEyzp4gRN1MbvXknD1ZuyT1+cC7rS+ZDZ3FhNn4/
wxvCQQS18G4zRkrUTes4X3fdi+n/APvyAwJBALncneqXzRR4Xx6HuGZ1DxZdpipj
x9cD5orMz4PGXrHeq+Vgs+nGdsvPeW3U1KZRsk7maRrI0QDmWGKGN6nRPskCQCPk
JWFZ3EWviJ93dZfFTN1cmrZAbAyNQOMsTcoKsDi+psVpERDXC+rpSLGjqVc6DbLw
OwDS4YykXgV0788ZrD0CQQCbe+VkCVX1Nyrqgylpnza+W75p+A5YUC7kZgvls2kG
sr5+BAyyOPpTiUao+l3ib15udCxJmw+qEYSq8TQEaLpG
-----END RSA PRIVATE KEY-----
-----BEGIN CERTIFICATE-----
MIICrzCCAhigAwIBAgIJAPQiP2Rt0I/qMA0GCSqGSIb3DQEBBQUAMFAxCzAJBgNV
BAYTAlVTMRAwDgYDVQQIEwdBcml6b25hMQwwCgYDVQQKEwNGQk4xCzAJBgNVBAsT
AkNBMRQwEgYDVQQDEwtOb2FoIERhdmlkczAeFw0wODA4MjQxNDEzMjlaFw0wOTA4
MjQxNDEzMjlaMGYxCzAJBgNVBAYTAlVTMRAwDgYDVQQIEwdBcml6b25hMRAwDgYD
VQQHEwdQaG9lbml4MQwwCgYDVQQKEwNGQk4xDzANBgNVBAsTBkNsaWVudDEUMBIG
A1UEAxMLTm9haCBEYXZpZHMwgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBAOFm
T2gXwHm31+LCxMEx14L1GqRMOhWYAWo6q1s4+guQUeF7oHq5Jz0tNbmq+bYI2N8f
ZaG1/uS9iPpE4+0/bPbIG3SAfLrz9FTjEjSOc+S9gNXJ7isGFgEEJ1E3WhIh+Bf4
quOw+204+9BWHg2cJnZBWp6WvIjLZevFHaqV1p47AgMBAAGjezB5MAkGA1UdEwQC
MAAwLAYJYIZIAYb4QgENBB8WHU9wZW5TU0wgR2VuZXJhdGVkIENlcnRpZmljYXRl
MB0GA1UdDgQWBBT/8RXhBFPlJnEQkLamP4yJuLy+/zAfBgNVHSMEGDAWgBQMHLhR
sNRb6uSwAv5dVYDXF/54PTANBgkqhkiG9w0BAQUFAAOBgQBJvzn9DxeU56SKXaVa
s1XyCJ0ty+cDdH/blg474uzJr25Hc3ZqWf4KBMuohqrHkAO4b1f1JwNMj1AetVxy
sk0Rahx1uCHjzCKHjtpuj1kc/+fjH2oEI1UYZKhSi1dG2f3v9BuYWjVCpgVEZLpz
LeLKl/bibAcAbHe3c9g73XWp+Q==
-----END CERTIFICATE-----
-----BEGIN RSA PRIVATE KEY-----
MIICXQIBAAKBgQCjFUVhee/3RvapaM+JyGETO1mZsBcQ/+k0W8IC/OClKc8hH1ML
YWCt7WuRTZ7tL6YGn/rfx0xlMiN65ebyrioV8W0t4g17CL3f5+e0UqiCUF1sUfW2
zVP0s+2UDyKFCX2lScY+4MHr6aE5fyKFkOSmQwjFYa+/MB5VICln4CYBGwIDAQAB
AoGAGAh4cwb/QBerHggeHZX0CFuEtstmetDb0yV6j+ooSO7CYYU2PcUZ9Ee6xG0F
8LpG408ML5I1Rex/ogrjX/weo2T5tsf7C0TxoJRUu4F6yQ8VUBbZ1z+2HZzw29Fi
y4pax8xUBYlU/aqBd0rqEZyNW40tDRjmrIfOH7t/wIng5ZECQQDMpP007DemQdN+
IQS+e/+q3TXkTjuGSXNoShqwCkJ0zUOBE4sWsCSCwWp2ZF44a7dx/of+050FAcH6
3DrDYdadAkEAzAI+8eR6JcLH0L7lsxKgLaDj/RwAZ7bDKaULXOes8pEMFePLxLN+
yY32QPQbZrUMAzo1mDJ0KrkiczD454DNFwJAf9nUF2w8mDIn33ThceAmKqlpMelu
ZsccwtsJMVI3kqFquwlqrBH/vXD5Al5SPw2M3jsW2615O9eNSRyt2cMWQQJBAIdB
+e+wlteQU6Bv4KUgdTirUl1PAmnA/5YNygHXzI+qYUPmGwSYKTiCucEI1136LTO6
lSwKT4C/7DpJPs1mVRMCQQCD8fqwCs0RWo9chugoHh3nrI9VXzDvglz2O5DGgdiS
RAwwWU5P0+G1m71jjeB447/bCHm+DzP2xHlIlh0Gf7Pr
-----END RSA PRIVATE KEY-----
-----BEGIN CERTIFICATE-----
MIIC0jCCAjugAwIBAgIJAPQiP2Rt0I/oMA0GCSqGSIb3DQEBBQUAMFAxCzAJBgNV
BAYTAlVTMRAwDgYDVQQIEwdBcml6b25hMQwwCgYDVQQKEwNGQk4xCzAJBgNVBAsT
AkNBMRQwEgYDVQQDEwtOb2FoIERhdmlkczAeFw0wODA4MjQxNDA1MzhaFw0xMTA4
MjQxNDA1MzhaMFAxCzAJBgNVBAYTAlVTMRAwDgYDVQQIEwdBcml6b25hMQwwCgYD
VQQKEwNGQk4xCzAJBgNVBAsTAkNBMRQwEgYDVQQDEwtOb2FoIERhdmlkczCBnzAN
BgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEAoxVFYXnv90b2qWjPichhEztZmbAXEP/p
NFvCAvzgpSnPIR9TC2Fgre1rkU2e7S+mBp/638dMZTIjeuXm8q4qFfFtLeINewi9
3+fntFKoglBdbFH1ts1T9LPtlA8ihQl9pUnGPuDB6+mhOX8ihZDkpkMIxWGvvzAe
VSApZ+AmARsCAwEAAaOBszCBsDAdBgNVHQ4EFgQUDBy4UbDUW+rksAL+XVWA1xf+
eD0wgYAGA1UdIwR5MHeAFAwcuFGw1Fvq5LAC/l1VgNcX/ng9oVSkUjBQMQswCQYD
VQQGEwJVUzEQMA4GA1UECBMHQXJpem9uYTEMMAoGA1UEChMDRkJOMQswCQYDVQQL
EwJDQTEUMBIGA1UEAxMLTm9haCBEYXZpZHOCCQD0Ij9kbdCP6DAMBgNVHRMEBTAD
AQH/MA0GCSqGSIb3DQEBBQUAA4GBAJZD6N595vcLXnB9EhKGWCDCuTvkuLcaE3Fh
dcecG+twYhTCnGwezVk+NgaqkxM2jR7unHv33yzbzAeINisOKX/iOkVmcffyLZ9y
2aw63R2st7kh2lv5JyrtfDkwcvI5a85LQ1fsQp6cRefyP/wbFD9tCt9lYX1W5p1q
VuENFsb3
-----END CERTIFICATE-----
stunnel_server_ca.pem
-----BEGIN RSA PRIVATE KEY-----
MIICXAIBAAKBgQDWRm2rMZmTQBvP9ocAWg3O9oFh/UktcabmNxrwS+/xeE5SSQ+A
gMrN1qwVxcqu7PA4htPzjD0/9qZEKXMIsQ0OyyzzgnKs/czh0VZ2irf+g8q/pmRu
/JD1SDsTz2S3AUzcgy0pY1cKGF90i0sDii7ORW4q/Fmzhn+bWp0UCL+tvQIDAQAB
AoGAJCu5YZe62/+LclykR2vsPs6f4qG2E6TGzr/onT3EYFe1qPBKXJ/hHEQrwnUk
FMlMd85Swx8eS8jgIkt47rOsh06tqrpQ26RiWfGYur1uKFuyt9l3qinGWQbkrxLq
f9WdKZGVcm1AEocaeBjkmkCzt9KqNiSH+64kGHkVV2R1TKUCQQDwOezR+2yLU6NS
ExwK4PweIGuJhOzRpeuBRuz1r0MTATvrWkqVOKXDuxiMA5CPCkutuIjRH9Z+SOLt
eExOA3kDAkEA5FhHOkxlpqen4Pf0eHXlFPNYqseuv6bHeZRgD++n/mDABfh+/RTu
xjzBjRbUBiKH88iW+ZZffl9u1hyloBuiPwJAcZJxLDU59ATuyfbO4zXK/FNHhBSc
AeH3nX7yuJTLmUiUE4j0iefmNstVp5xn07iCXvdHd9cdiUbcQnkFWjy6EQJBAM+z
bLaenyfEAHQlln2r3z/7SX+uOkmhjngMeoSEXa6ImqHTss7Jp5cx1Gxdg2ZBKqCY
qJtGKH5umAax8AV+nUkCQGux+PFHy+P7v1KcShKvsDUCo81wh839inVA1HqoXF+y
rwdaxsqI8QH7pPgBHN3PpwIwHbrG0vrivRn2xGASaFA=
-----END RSA PRIVATE KEY-----
-----BEGIN CERTIFICATE-----
MIICrzCCAhigAwIBAgIJAPQiP2Rt0I/pMA0GCSqGSIb3DQEBBQUAMFAxCzAJBgNV
BAYTAlVTMRAwDgYDVQQIEwdBcml6b25hMQwwCgYDVQQKEwNGQk4xCzAJBgNVBAsT
AkNBMRQwEgYDVQQDEwtOb2FoIERhdmlkczAeFw0wODA4MjQxNDA3MzhaFw0wOTA4
MjQxNDA3MzhaMGYxCzAJBgNVBAYTAlVTMRAwDgYDVQQIEwdBcml6b25hMRAwDgYD
VQQHEwdQaG9lbml4MQwwCgYDVQQKEwNGQk4xDzANBgNVBAsTBlNlcnZlcjEUMBIG
A1UEAxMLTm9haCBEYXZpZHMwgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBANZG
basxmZNAG8/2hwBaDc72gWH9SS1xpuY3GvBL7/F4TlJJD4CAys3WrBXFyq7s8DiG
0/OMPT/2pkQpcwixDQ7LLPOCcqz9zOHRVnaKt/6Dyr+mZG78kPVIOxPPZLcBTNyD
LSljVwoYX3SLSwOKLs5Fbir8WbOGf5tanRQIv629AgMBAAGjezB5MAkGA1UdEwQC
MAAwLAYJYIZIAYb4QgENBB8WHU9wZW5TU0wgR2VuZXJhdGVkIENlcnRpZmljYXRl
MB0GA1UdDgQWBBRr0bGphNWQHP12dOU/pOd+rB1YXzAfBgNVHSMEGDAWgBQMHLhR
sNRb6uSwAv5dVYDXF/54PTANBgkqhkiG9w0BAQUFAAOBgQBwOdctmkhERLTMJW8G
viC0MwBt8foTEU/Z6geixeIJEM/iyy1b4ET2S9xr3zhuZ8mCI7ZeMtVWf4R0roP1
2kDYtvRTtVioCXgNxxsUMg+gCxNMmJ2jGHFwaaGux1EOPqtn6RUaL/Xyb/ttHJj2
h9BTKeG3jW+rJZ6iqr79VC2Zgg==
-----END CERTIFICATE-----
-----BEGIN RSA PRIVATE KEY-----
MIICXQIBAAKBgQCjFUVhee/3RvapaM+JyGETO1mZsBcQ/+k0W8IC/OClKc8hH1ML
YWCt7WuRTZ7tL6YGn/rfx0xlMiN65ebyrioV8W0t4g17CL3f5+e0UqiCUF1sUfW2
zVP0s+2UDyKFCX2lScY+4MHr6aE5fyKFkOSmQwjFYa+/MB5VICln4CYBGwIDAQAB
AoGAGAh4cwb/QBerHggeHZX0CFuEtstmetDb0yV6j+ooSO7CYYU2PcUZ9Ee6xG0F
8LpG408ML5I1Rex/ogrjX/weo2T5tsf7C0TxoJRUu4F6yQ8VUBbZ1z+2HZzw29Fi
y4pax8xUBYlU/aqBd0rqEZyNW40tDRjmrIfOH7t/wIng5ZECQQDMpP007DemQdN+
IQS+e/+q3TXkTjuGSXNoShqwCkJ0zUOBE4sWsCSCwWp2ZF44a7dx/of+050FAcH6
3DrDYdadAkEAzAI+8eR6JcLH0L7lsxKgLaDj/RwAZ7bDKaULXOes8pEMFePLxLN+
yY32QPQbZrUMAzo1mDJ0KrkiczD454DNFwJAf9nUF2w8mDIn33ThceAmKqlpMelu
ZsccwtsJMVI3kqFquwlqrBH/vXD5Al5SPw2M3jsW2615O9eNSRyt2cMWQQJBAIdB
+e+wlteQU6Bv4KUgdTirUl1PAmnA/5YNygHXzI+qYUPmGwSYKTiCucEI1136LTO6
lSwKT4C/7DpJPs1mVRMCQQCD8fqwCs0RWo9chugoHh3nrI9VXzDvglz2O5DGgdiS
RAwwWU5P0+G1m71jjeB447/bCHm+DzP2xHlIlh0Gf7Pr
-----END RSA PRIVATE KEY-----
-----BEGIN CERTIFICATE-----
MIIC0jCCAjugAwIBAgIJAPQiP2Rt0I/oMA0GCSqGSIb3DQEBBQUAMFAxCzAJBgNV
BAYTAlVTMRAwDgYDVQQIEwdBcml6b25hMQwwCgYDVQQKEwNGQk4xCzAJBgNVBAsT
AkNBMRQwEgYDVQQDEwtOb2FoIERhdmlkczAeFw0wODA4MjQxNDA1MzhaFw0xMTA4
MjQxNDA1MzhaMFAxCzAJBgNVBAYTAlVTMRAwDgYDVQQIEwdBcml6b25hMQwwCgYD
VQQKEwNGQk4xCzAJBgNVBAsTAkNBMRQwEgYDVQQDEwtOb2FoIERhdmlkczCBnzAN
BgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEAoxVFYXnv90b2qWjPichhEztZmbAXEP/p
NFvCAvzgpSnPIR9TC2Fgre1rkU2e7S+mBp/638dMZTIjeuXm8q4qFfFtLeINewi9
3+fntFKoglBdbFH1ts1T9LPtlA8ihQl9pUnGPuDB6+mhOX8ihZDkpkMIxWGvvzAe
VSApZ+AmARsCAwEAAaOBszCBsDAdBgNVHQ4EFgQUDBy4UbDUW+rksAL+XVWA1xf+
eD0wgYAGA1UdIwR5MHeAFAwcuFGw1Fvq5LAC/l1VgNcX/ng9oVSkUjBQMQswCQYD
VQQGEwJVUzEQMA4GA1UECBMHQXJpem9uYTEMMAoGA1UEChMDRkJOMQswCQYDVQQL
EwJDQTEUMBIGA1UEAxMLTm9haCBEYXZpZHOCCQD0Ij9kbdCP6DAMBgNVHRMEBTAD
AQH/MA0GCSqGSIb3DQEBBQUAA4GBAJZD6N595vcLXnB9EhKGWCDCuTvkuLcaE3Fh
dcecG+twYhTCnGwezVk+NgaqkxM2jR7unHv33yzbzAeINisOKX/iOkVmcffyLZ9y
2aw63R2st7kh2lv5JyrtfDkwcvI5a85LQ1fsQp6cRefyP/wbFD9tCt9lYX1W5p1q
VuENFsb3
-----END CERTIFICATE-----
4) configure stunnel
Stunnel comes with a default configuration file. There are only a few changes you need to make but they are slightly different for the client and server. When you install stunnel one of the start/programs/stunnel menu entries is "edit stunnel.conf. It brings up the stunnel.conf file in notepad.
verify = 3
cert = stunnel_server.pem
CAfile = stunnel_client_ca.pem
[stunnel]
accept = 119
connect = 127.0.0.1:8008
verify = 3
cert = stunnel_client.pem
CAfile = stunnel_server_ca.pem
[stunnel]
accept=8080
connect=192.168.1.50:119
; Sample stunnel configuration file by Michal Trojnara 2002-2006
; Some options used here may not be adequate for your particular configuration
; Certificate/key is needed in server mode and optional in client mode
; The default certificate is provided only for testing and should not
; be used in a production environment
;cert = stunnel.pem
;key = stunnel.pem
; Some performance tunings
socket = l:TCP_NODELAY=1
socket = r:TCP_NODELAY=1
; Workaround for Eudora bug
;options = DONT_INSERT_EMPTY_FRAGMENTS
; Authentication stuff
;verify = 2
; Don't forget to c_rehash CApath
;CApath = certs
; It's often easier to use CAfile
;CAfile = certs.pem
; Don't forget to c_rehash CRLpath
;CRLpath = crls
; Alternatively you can use CRLfile
;CRLfile = crls.pem
; Some debugging stuff useful for troubleshooting
debug = 7
;output = stunnel.log
; Use it for client mode
;client = yes
verify = 3
cert = stunnel_server.pem
CAfile = stunnel_client_ca.pem
; Service-level configuration
;[pop3s]
;accept = 995
;connect = 110
;[imaps]
;accept = 993
;connect = 143
;[ssmtp]
;accept = 465
;connect = 25
;[https]
;accept = 443
;connect = 80
;TIMEOUTclose = 0
; vim:ft=dosini
[stunnel]
accept = 119
connect = 127.0.0.1:8008
; Sample stunnel configuration file by Michal Trojnara 2002-2006
; Some options used here may not be adequate for your particular configuration
; Certificate/key is needed in server mode and optional in client mode
; The default certificate is provided only for testing and should not
; be used in a production environment
;cert = stunnel.pem
;key = stunnel.pem
; Some performance tunings
socket = l:TCP_NODELAY=1
socket = r:TCP_NODELAY=1
; Workaround for Eudora bug
;options = DONT_INSERT_EMPTY_FRAGMENTS
; Authentication stuff
;verify = 2
; Don't forget to c_rehash CApath
;CApath = certs
; It's often easier to use CAfile
;CAfile = certs.pem
; Don't forget to c_rehash CRLpath
;CRLpath = crls
; Alternatively you can use CRLfile
;CRLfile = crls.pem
; Some debugging stuff useful for troubleshooting
;debug = 7
;output = stunnel.log
; Use it for client mode
client = yes
verify = 3
cert = stunnel_client.pem
CAfile = stunnel_server_ca.pem
; Service-level configuration
;[pop3s]
;accept = 995
;connect = 110
;[imaps]
;accept = 993
;connect = 143
;[ssmtp]
;accept = 465
;connect = 25
;[https]
;accept = 443
;connect = 80
;TIMEOUTclose = 0
; vim:ft=dosini
[stunnel]
accept=8080
connect=192.168.1.50:119
5) start stunnel and the web proxy on the home system
Once the changes are made to stunnel.conf you can start stunnel and also the webscarab. With the above stunnel settings you can use the default Webscarab configuration.
6) start stunnel on the laptop
There should be an option under Start/Programs/stunnel to "run stunnel", use this option to start stunnel on the laptop.
7) configure the laptop browser to use a web proxy
Configure your laptop's browser to use a proxy with an IP address of 127.0.0.1 and a port of 8080. This is the accept port that stunnel on the laptop is configured to use.
One small issue
Because you are using a web proxy when you go to secure, aka HTTPS, sites like your bank, your browser will issue a warning that the certificate does not match the bank. It will report that certificate belongs to webscarab. You will have to set up an exception to continue, As long as the certificate belongs to the proxy you are using this is fine.
That's it your done. E-mail and banking are now secure.
![]()
This page was last modified on 08-08-30![]() Send comments and suggestions
Send comments and suggestions
to ndav1@cox.net